In September, ProLink Director, Phillip Harrington spoke at the National Association of Corporate Directors Global Leaders’ Summit on the “Cyber Disclosure, Liability, and Reputation Risk” panel. Since cyber security is something very important to us at ProLink, when he returned we sat down with him to go over what he spoke about, as well as what he learned from the other panel members on the subject in order to provide you with more information. Keep reading below for the full interview!
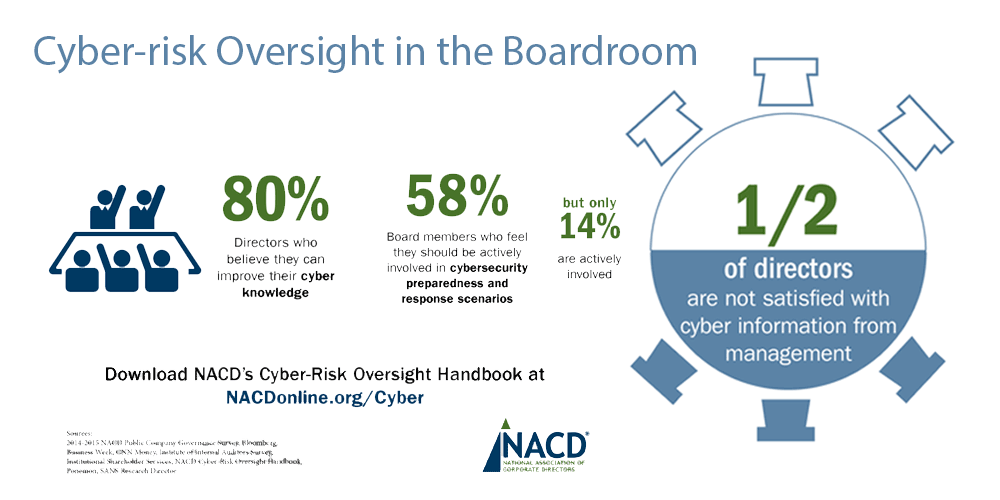
Source: NACD Strategy and Risk Forum
Phil, you recently spoke at the annual meeting of the National Association of Corporate Directors in Washington, D.C. on the topic of cyber disclosure, liability and reputation risk. Based on your experiences as an executive and a member of both for-profit and non-profit boards, what should board members be asking of their executive teams to ensure an appropriate level of cyber security and preparedness?
Cyber security has certainly emerged as one of the hot topics in virtually every boardroom. From a director’s perspective, I think there are three key considerations that help put the issue of cyber security into some context. First, I believe it is very important for directors to keep in mind it that the vast majority of cyber incidents have root causes that are internal and self-induced, rather than being external and malicious. Second, there is a very large strategic risk to companies that fail to innovate or delay pursuing critical business objectives because of cyber fears or perhaps a lack of certain skill sets and experiences; and third, and closely related to these first two considerations, I think the board has a heightened obligation to both understand and participate in setting the organization’s appetite for cyber risk and digital innovation just as it does with other enterprise risks.
So, with that as context, there are five tangible things I believe boards should expect from their executive teams, at a minimum:
- Clear evidence of a thoughtful identification and assessment of the organization’s key information assets, i.e., the “crown jewels”
- A current and dynamic “stem to stern” IT risk assessment using one of the available frameworks – like the NIST – that is tied to the organization’s key information assets
- Utilization of third party assessments, such as penetration testing, importantly with the results discussed with the board;
- A current, detailed and thoroughly tested incident response plan
- An alignment of executive roles and organizational positioning that reflects the new reality, such as the reporting chain of the CIO, frequency of board interaction with CIO, etc.
“…it is very important for directors to keep in mind it that the vast majority of cyber incidents have root causes that are internal and self-induced, rather than being external and malicious.” [Tweet This]
What do you mean by this last point?
Questions like, does the CISO have regular contact with the CEO? Historically, most CISOs have had no regular contact with their CEO. Also, does the CISO or CIO have authority to stop a business initiative because of serious security concerns?
As it relates to the board specifically, do directors meet in executive session with the CIO and/or CISO? I would assert that such interaction ought to increasingly emulate that of director’s interaction with other c-suite executives, including the CFO. Also, does the board explicitly review and approve the company’s cyber security policy?
Performance incentives for CIO are also something that boards should make inquiry into —for instance, in the past, CIO incentives were based on things like based on system uptime and reducing IT spend year-over-year. I believe it is time to revisit how we incent CIO performance to recognize the current and future reality.
That’s really helpful. I know you also talk a lot about the importance of culture. How does culture influence an organization’s cyber preparedness?
Great question. There are at least two critical factors that will greatly enhance the effectiveness of the tangible items I just mentioned in terms of helping a company mitigate liability and reputational damage from cyber incidents.
First, the board must be assured that the executive team collectively sees itself as having primary accountability for cyber risk, and not just the CIO or CISO. The single biggest driver of maturing the management of cyber security risks is senior management’s time and attention — more important than company size, company sector, and even budget.
Second, the organizational culture must encourage and reward timely and fulsome identification of risks and the upward reporting of incidents and concerns. I’ve seen organizations over and over get into difficult and even catastrophic situations because of cultures that just didn’t have the capacity to receive and deal with bad news from the middle of the organization.
“The single biggest driver of maturing the management of cyber security risks is senior management’s time and attention.” [Tweet This]
Recognizing that companies can’t do everything, it seems a key challenge is being selective about where to focus cyber security investments. How can boards size up such investments bearing in mind key stakeholder expectations and risk tolerances?
I believe a significant gap exists in the quality of the dialogue between boards and management in relation to the board’s role in helping management calibrate its risk tolerance around information and technology risks generally. What I mean by this is that boards are engaged in a regular, well-understood dialogue with management as it relates to goal setting around financial targets, sales targets, etc., and both management and the governing bodies generally have a clear and common understanding of those standards and targets.
Boards also regularly discuss with management the organization’s risk appetite in areas like internal controls and financial performance objectives.
Where the gap exists that I’ve seen both as a board member and as a member of executive management is in the area of cyber risk. It seems like we have a tendency as board members to behave differently when discussing cyber risks; that looking at cyber risks is somehow different from other types of enterprise risks.
But isn’t cyber risk something that’s emerging and evolving rapidly and therefore not like other enterprise risks?
Yes, but I don’t see that as a reason to treat cyber risk any differently than we do other risks. In fact, we can inadvertently create greater risk to the organization to the extent we try to segregate cyber risk from other risks facing the organization.
The challenge I’ve seen is that many of us may perceive cyber risks as being highly technical and arcane. That works against us as board members. The result is we may lack the same intensity of discussion around digital risks relative to other risks.
“The cost of malicious cyber activity involves more than the loss of financial assets or intellectual property. There are opportunity costs, damage to brand and reputation, consumer losses from fraud, the opportunity costs of service disruptions “cleaning up” after cyber incidents and the cost of increased spending on cybersecurity,” states the Center for Strategic and International Studies
But some cyber risks are pretty arcane and technical.
True. But it doesn’t necessarily follow that the board dialogue needs to be arcane and technical. In fact, boards should expect the dialogue about cyber risk to be in plain, understandable language. Further, a primary board role is to help management make risk trade off decisions, which does not require diving into the IT weeds.
For instance, the loss of IP to a foreign competitor, disclosure of confidential customer information, and business disruptions like that faced earlier this year by New York Stock Exchange are all troubling events, but which is most important? If the organization spends another $50 million on cyber risk mitigation, but can’t quantify the risk reduction, should it spend the $50 million anyway? These are critically important decisions that are being made every day by management, but that I believe should be informed through ongoing dialogue with the board. The CEO and board must be in a dialogue about calibrating risk appetite and tolerance for different types of adverse cyber events.
It sounds like you are suggesting that boards have to get into the weeds on IT spending.
I think a useful discussion to have with the CEO is how he or she makes decisions around IT spend both in isolation as well as in relation to all other resource allocation decisions. I’m also interested in knowing the types of trade-off decisions that have been made over the past several years. Until recently it was common for IT budgets to be reduced year-over-year and to view IT as a cost center to be managed down, and not a strategic asset in valuation creation that at the same time poses a significant risk. For obvious reasons, that perspective is now changing to a degree.
I am of the belief that the root cause of a majority of cyber events are in the resource allocation decisions made by management. And, this is generally not a question of not spending enough. Many, if not most cyber risks can be mitigated by internal resource allocation decisions. It is one thing to have consultants, penetration testing, quite another to make resource allocation decisions. Management makes cyber risk trade-off decisions all the time: things like IT budgets or related decisions like deferring upgrades to an organization’s IT hardware or software application environment. Other examples include employee training, assigning roles like business continuity planning too low in the organization, or placement of the CIO in the organization. Most of these decisions occur – appropriately — away from view of the board. But, at the same time, I believe that boards need to play a greater role in helping management calibrate risk tolerances and appetites as it relates to cyber risks. The board needs to satisfy itself that management is not overly focused on “hitting the numbers” at the expense of managing cyber risk.
“…a useful discussion to have with the CEO is how he or she makes decisions around IT spend both in isolation as well as in relation to all other resource allocation decisions.” [Tweet This]
But isn’t this just like any other trade-off discussion that management regularly engages in?
On the surface, yes. However, the very quickly changing nature of cyber risks to organizations, particularly reputational risk, necessitates a different level of dialogue between management and the board. Boards need to ensure that the CEO and his or her colleagues understand clearly the boards’ appetite for various categories of cyber risks so that management and the board are aligned.
Let’s say the CIO of a large company recommends spending $300 million to mitigate cyber risk, but can’t quantify precisely the aggregate risk reduction to the company. If that $300 million would a reduction in the company’s net operating margin from 30% to 28%, is that a good decision and how do you decide? That kind of decision, in my view, should be made with the board and not left solely to management.
Even with thoughtful cyber risk management, some attacks will be successful. Can you comment on how boards should engage around the planning process to ensure that organizations are ready when the inevitable happens?
First, make sure management has a plan. Then, make sure it is detailed, dynamic and thoroughly tested. I’ve seen many examples where plans are outdated, general, not tested, and with accountability relegated too low in the organization, which can essentially render any such “plan” useless in the event of an actual incident.
Second, if management thinks it has a great plan, I’d ask them to think again. Here, my question would not be “does our company have a cyber incident response plan” but, rather, “tell me about the last time you table top exercised the response plan, what the results were, and how you changed the plan as a result?”
Want to learn more about how we keep your data secure on Procorem? Click here to head to our Help Center for more information on this topic and more! As always, we’d love to hear your thoughts on the subject so please comment below or send us an email at contact@www.procorem.com.

 Procorem was built with the understanding that no matter the industry, business is conducted human-to-human—and our processes and tools ought to reflect it.
Procorem was built with the understanding that no matter the industry, business is conducted human-to-human—and our processes and tools ought to reflect it.